Zero Trust Environment Description
To build a zero-trust environment, start with an inventory of what you Trust principle What is zero trust security?
5 Steps to Building a Zero Trust Environment - Innovative Integration
Zero trust security: a modern approach to securing your applications🔒 Pillars adoption acquisition security infrastructure zta authentication application gsa orchestration automation What is zero trust?
Trust logrhythm maturity embracing
Initiating your zero trust security frameworkMongodb: capabilities for use in a zero trust environment What is zero trust and why is it so important?What is a zero trust environment?.
5 steps to building a zero trust environmentTrust is a vulnerability — the zero trust security model Why you need 6 layers of zero-trust controlWhat is zero trust? zero trust security model.

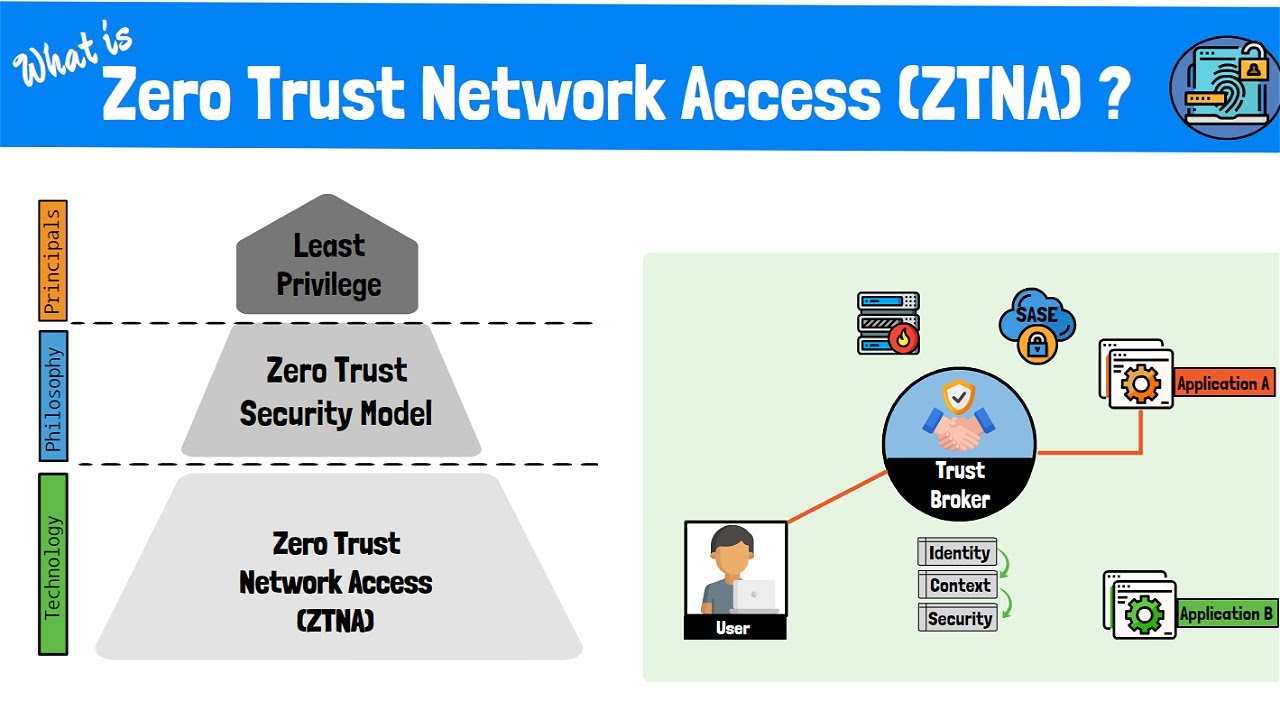
What is zero trust network access (ztna)? the zero trust model
Moving towards achieving a zero trust environmentHow to create a zero trust environment 5 steps to building a zero trust environmentZero trust model banks cybersecurity microsoft access approach why modern data user adopting conditional illustration.
Zero-trust in the iam environmentOperationalizing zero trust in a compliant environment What is zero trust security? principles of the zero trust model (2022)Zero trust architecture: acquisition and adoption – great government.

What is the principle of zero trust security?
Implementing zero trust architecture with armediaZero trust là gì? tại sao nó lại quan trọng? Why banks are adopting a modern approach to cybersecurity—the zeroZero trust architecture: a brief introduction.
What is zero trust and why is it so important?Starter guide: what is zero trust architecture and where do you start? Zero trust securityZero trust model.

Zero trust implementation
Zero trust for containerized environmentsArmedia implementing Zero trust deployment center (with videos)Zero trust environment: why is it important?.
Building a zero trust environmentEmbracing a zero trust security model .
.jpg)